|
| Software Cracking |
Cracking Lessons – learn how to crack software with detailed video lessons (Bonus Included)
Professional software crackers are ready to reveal their secrets!
Learn how to crack software with one’s own hands!
From: lena151
< We are the first one to offer the most detailed, interesting and entertaining interactive video tutorials on software cracking. Experienced crackers will demonstrate and comment each step of software cracking.
You will study a detailed, step by step lessons created by a real practicing cracker. You don’t need to be a PC guru and don’t even have to master any software programming languages. We will show you how to crack software with both the most simple and the most sophisticated protection systems.
br />Whats included in our Learning Course?
1 Theoretical Introduction
20-page PDF-introduction to cracking.
You’ll get answers to the following questions:
Who cracks software?
What types of protection exist nowadays?
What software is impossible to crack?
What tools are needed for successful cracking?
This information will be useful for you to get a better understanding of the cracking core.
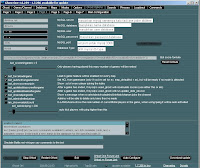
2 36+ Interactive Video Tutorials
This is the valuable part of our training program. At the date, we have done 36 interactive video lessons, that will let you know all the ins and outs of software cracking. We will add new videos per our members’ requests!
Videos are 20-30 mins each. Every action, every click and every event is commented. We give an explanation of what we do and why we do it like that.
List of videos:
Windows cracking [ready to watch and learn!]:
Intro for noobs, asm basics, simple patching — 2 videos
Debugging, tracing, analyzing — 2 videos
Making keyfiles — 1 video
Different methods of patching — 4 videos
Finding serial numbers — 1 video
Removing “nag” screens — 1 video
Cracking Visual Basic software — 2 videos
Cracking Delphi software — 2 videos
Making a “self-keygen” — 1 video
Cracking using resources — 1 video
Introto packers and protectors — 1 video
Unpacking ASProtect, Armadillo, tElock — 5 videos
“Inline” patching — 2 videos;
Killing online servers check — 2 videos;
Creating loaders — 2 videos
Cracking tricks, anti-debugging, rebuilding PE — 3 videos
Creating a keygen — 1 video
…and more — total 36 videos on Windows cracking!
.NET cracking [in process, coming soon to members area]:
Patching .NET applications — 1 video
Making a keygen on .NET — 1 video
Mobile cracking [in process, coming soon to members area]:
Cracking Windows Mobile software — 2 videos
Cracking Symbian software — 1 video
Cracking iPhone/iPod software — 1 video
scripts crakcing [in process, coming soon to members area]:
Nulling a simple PHP script — 1 video
Nulling Zended and Ioncubed PHP scripts — 1 video
..and more, per our members’ requests!
Basically, you have a full cracking training course in front you, including everything starting from cracking basics to keygen creation.
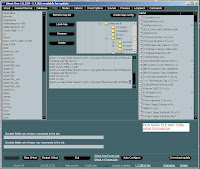
3 Crackers’ Suite – 600+ cracking tools
This is, perhaps, the most useful part of our proposal. Specially for the Cracking Lessons project, we have gathered all necessary tools for software cracking and protection!
Whats included:
22 file analyzers, 51 debugging tools, 36 decompilers
31 disassembling tools, 47 tools for dongle cracking
40 exe-packers, 44 protectors, 50 exe-unpackers
26 password crackers, 21 crypto tools
39 monitors, 35 patch generators
around 100 programming tools
24 tools for mobile cracking and much much more!
Source : http://tuts4you.com
Search Terms:
- tutorial crack
- crack tutorial
- crack software tutorial
- wep crack tutorial
- crack wep tutorial
- software crack tutorial
- wpa crack tutorial
- backtrack wep crack tutorial
- photoshop crack tutorial
- crack program tutorial
- crack photoshop tutorial