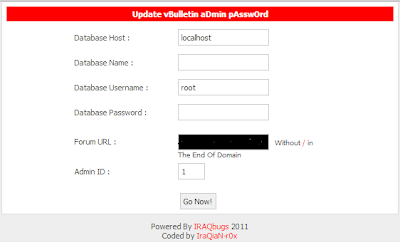
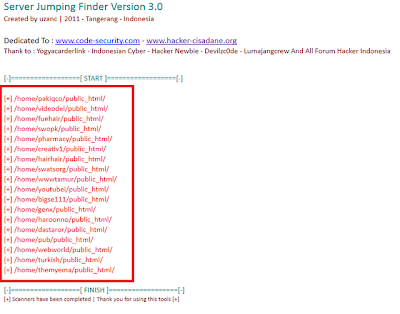
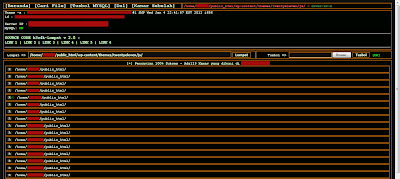
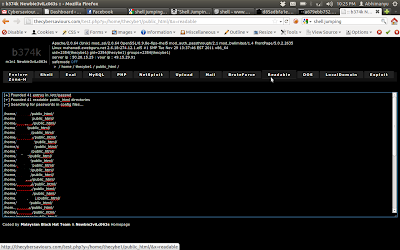
Jumping / Bypassing Symlink Shell Linux Script PHP, This method is used to access folders / files on server based linux which user not permitted or forbidden, So by Bypassing symlink A user can access files or folder either open configuration file in order to connect to the database. Now Time to share Symlink Shell Linux Script coded PHP.
 |
| Jumping / Bypassing Symlink Shell Linux Script PHP |
How to use Symlink bypass Shell script:
- Download the file sym.zip and Upload it into your shell
- Extract first command unzip sym.zip
- Run it Put symlink link ex : http://site.org/sym.php
- Click on User & Domain & Symlink
- Clink symlink and it will open directory of that user
Search Terms :
- symlink
- remove symlink
- symlink linux
- linux symlink
- create symlink
- windows symlink
- symlinks
- symlink windows
- unix symlink
- windows 7 symlink
- ubuntu symlink
- symlink ubuntu
- python symlink
- symlink unix
- perl symlink
- symlink directory
- linux create symlink
- delete symlink
- symlink windows 7
- create symlink linux
- chown symlink
- create a symlink
- make symlink
- samba follow symlinks
- git symlinks
- php symlink
- change symlink
- linux remove symlink
- windows symlinks
- git symlink
- python os.symlink
- apache symlinks
- svn symlink
- rsync symlinks
- windows 7 symlinks
- puppet symlink
- rsync symlink
- apache symlink
- ant symlink
- symlinks windows 7
- create sym link
- find broken symlinks
- apache follow symlinks
- find symlinks
- remove a symlink
- rm symlink
- creating symbolic links
- follow symlinks
- linux symlinks
- samba symlinks
- osx symlink
- creating a symlink
- symlink php
- symlinking
- rsync follow symlinks
- windows xp symlink
- os.symlink
- symlinks linux
- ntfs symlink
- symlink ln
- creating symlink
- os x symlink
- symlinker
- ln -s symlink
- linux symlink directory
- unix create symlink
- android symlink
- creating symlinks
- symlink in windows
- php database tutorial
- free proxy software
- symlinks in windows
- php software download
- php programming tutorial
- linux make symlink
- symlink osx
- man symlink
- python free download
- symlink folder
- download free proxy
- symlink syntax
- find follow symlinks
- symlink windows xp
- php database connection
- samba symlink
- tomcat follow symlinks
- create symbolic links
- symlinks windows
- ln symlink
- make a symlink
- free download proxy
- symlink attack
- proxy free download
- create symlinks
- create symlink windows
- shell script bash
- linux symlink example
- symlink android
- linux tutorials for beginners
- linux find symlinks
- symlink creator